Ethical Hacking: Hacking Databases with Stone River eLearning
6,00 $
You may check content proof of “Ethical Hacking: Hacking Databases with Stone River eLearning” below:
Ethical hacking: hacking databases – Stone River eLearning
In the rapidly evolving landscape of cybersecurity, ethical hacking emerges as a critical skill set for both fledgling and seasoned IT professionals. Stone River eLearning’s course on “Ethical Hacking: Hacking Databases” is precisely tailored to equip learners with the essential expertise required to understand, exploit, and secure various database systems. This course is an intriguing gateway for individuals aspiring to enter the cybersecurity realm and for those aiming to enhance their existing knowledge.
Offering a rich amalgamation of theoretical knowledge and practical skills, it delves into vital areas such as SQL injection techniques, database vulnerabilities, security architectures, and data collection methodologies. As organizations face increasingly sophisticated cyber threats, the need for competent ethical hackers who can protect sensitive information has become paramount, with the potential for lucrative career opportunities exceeding six figures. Students will not just absorb information but will also engage in practical exercises to implement what they’ve learned immediately.
Course description and goals
The “Ethical Hacking: Hacking Databases” course by Stone River eLearning is structured to provide learners with a robust foundation in understanding the intricacies of database security. Through a mixture of lectures and hands-on activities, students will explore critical aspects such as the fundamentals of database threats, ethical hacking techniques tailored to various database systems (including Microsoft SQL, MySQL, and Oracle RDBMS), and the essential skills needed to mitigate these risks effectively.
The course aims to achieve several key goals:
- Knowledge acquisition: Equip students with a comprehensive understanding of database security principles and ethical hacking practices.
- Skill enhancement: Provide practical, hands-on exercises that reinforce learning and prepare students for real-world applications.
- Certification readiness: Prepare participants for important industry certifications like the EC-Council Certified Ethical Hacker and CompTIA Security+.
- Career growth: Address the high demand for cybersecurity professionals, with over a million global job openings, illustrating ample opportunities for career advancement.
The commitment to interactive learning and immediate application ensures a well-rounded educational experience, built on a foundation of understanding and practical skills.
Target audience
The course is ideally directed at a diverse audience, encompassing a variety of individuals eager to embark on or progress within the cybersecurity sphere. Here’s a closer look at the profile of the target audience:
- Beginners: Individuals with little or no prior knowledge of ethical hacking or cybersecurity who desire a comprehensive introduction to the world of database security. The course welcomes novices, providing a stepping stone into a complex field.
- IT professionals: Established tech experts looking to upgrade their skills and acquire specialized knowledge related to database vulnerabilities and security measures. This group may seek to enrich their resume with certification and practical experience that aligns with industry demands.
- Aspiring ethical hackers: Individuals determined to craft their careers as ethical hackers or penetration testers. This course offers them the toolkit needed to analyze databases, exploit vulnerabilities, and secure sensitive data effectively.
- Tech-savvy learners: Anyone eager to delve deeper into cybersecurity concepts and methodologies. This includes software developers, system administrators, or database managers who recognize the importance of understanding security principles related to the systems they work with.
In essence, this course provides an opportunity for a wide range of learners to engage with vital content that is applicable in today’s job market, characterized by rapid technological advancements and ever-evolving threats.
Course structure
The “Ethical Hacking: Hacking Databases” course boasts a meticulously curated structure that seamlessly guides learners through a comprehensive curriculum. In establishing an effective framework for understanding ethical hacking concepts and practices, the structure blends theoretical knowledge with practical application.
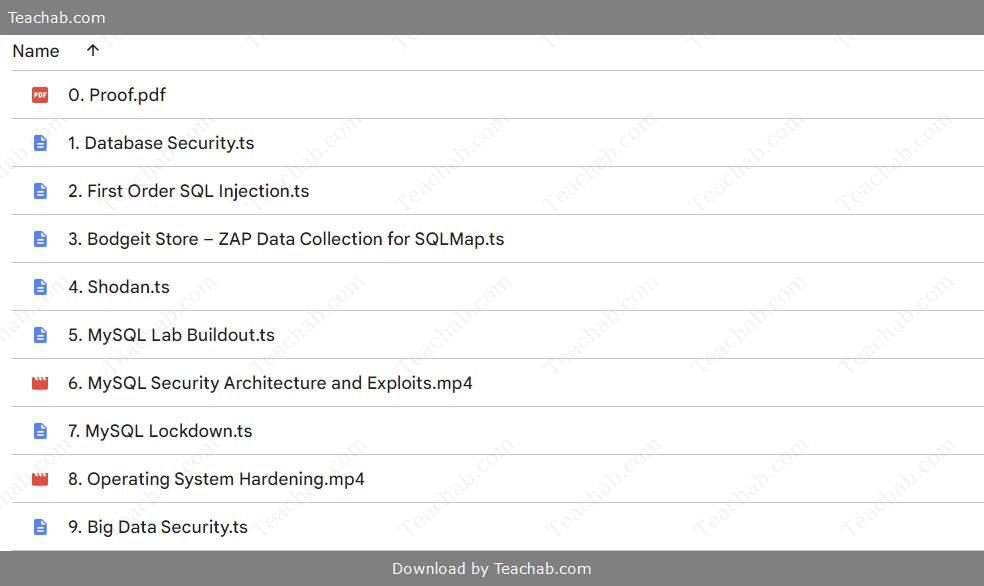
- Module Organization: Each module addresses specific aspects of database security and ethical hacking, ensuring a focused learning experience. Here’s a snapshot of the modules included:
- Database Security Overview
- First Order SQL Injection
- Data Collection Techniques using ZAP and SQLMap
- MySQL Lab Buildout
- Operating System Hardening
- Big Data Security
- Hands-On Experience: Real-world exercises at the end of each chapter allow students to test their skills right away. This not only reinforces learning but also helps students gain confidence as they apply their knowledge.
- Time Investment: The course is designed to be flexible, allowing students to progress at their own pace. The videos vary in length, facilitating both quick refreshers and in-depth explorations of complex topics.
- Supportive Materials: Additional resources, such as guides and supplementary readings, enrich the learning experience and ensure that students have the tools necessary to grasp and implement ethical hacking techniques effectively.
Overall, the course structure promotes an engaging learning experience that adapts to the needs of different learners, enhancing both comprehension and skill development.
Curriculum breakdown
The curriculum of the “Ethical Hacking: Hacking Databases” course is comprehensive, ensuring an in-depth understanding of crucial topics within the realm of ethical hacking, particularly in relation to databases. Here’s a detailed breakdown of the core modules covered:
- Database Security (20:11): This foundational module introduces students to the principles and practices surrounding database security, outlining essential strategies to protect data from unauthorized access.
- First Order SQL Injection (1:29): Students will learn about SQL injection a prevalent vulnerability that allows attackers to execute arbitrary SQL code on a database. This understanding is key to mitigating threats.
- Bodgeit Store – ZAP Data Collection for SQLMap (2:24): This practical lesson utilizes ZAP (Zed Attack Proxy) to gather exploitable data from a sample web application known as Bodgeit.
- Shodan (2:41): This lecture dives into Shodan, a unique search engine for internet-connected devices, providing insights into how it can be used for reconnaissance and vulnerability exploration.
- MySQL Lab Buildout (7:23): In this hands-on segment, students will create a lab environment for testing security measures in MySQL databases, reinforcing theoretical lessons.
- MySQL Security Architecture and Exploits (16:32): This module explores the security architecture of MySQL, with discussions about common vulnerabilities that can be exploited through SQL injection.
- MySQL Lockdown (35:08): Here, learners will review strategies for securing MySQL installations and implement hardening techniques to prevent attacks.
- Operating System Hardening (7:44): This lesson emphasizes the need to secure the operating system hosting the database and discusses the interplay between OS and database security.
- Big Data Security (17:33): The focus shifts to larger datasets in this part of the curriculum, highlighting security considerations and methods to protect data in big data environments.
This comprehensive structure ensures that students gain not only theoretical insights but also practical experiences that will make them confident in their skills as ethical hackers, which is vital for improving overall cybersecurity.
Database security
Database security is the cornerstone of effective ethical hacking, as it encompasses the methods and strategies employed to protect databases from unauthorized access and attacks. Understanding database security involves grasping the potential threats and vulnerabilities that could compromise sensitive information.
Types of Threats: Databases face various threats, such as SQL injection, unauthorized access, and data breaches. Recognizing these potential dangers is akin to understanding the vulnerabilities of a fortress before attempting to fortify its defenses.
- Access Control: Implementing strict access controls is vital. Organizations must ensure that only authorized users can access specific data. Role-based access control and auditing logs play a significant role in maintaining security.
- Encryption: Data encryption is a powerful tool for safeguarding sensitive information. Just as a locked vault protects valuables, encryption renders data unreadable to unauthorized users, thereby mitigating the risks of data breaches.
- Regular Updates and Patching: Keeping a database system updated minimizes vulnerabilities. Regular patching is similar to maintaining a sturdy wall that is checked and reinforced against potential break-ins.
- Backup and Recovery: A robust backup strategy is indispensable. In the event of a breach or data corruption, having secure backups allows organizations to recover lost information without catastrophic consequences.
By encompassing these principles, database security provides a strong foundation for ethical hackers, enabling them to identify weaknesses in systems, recommend improvements, and contribute to the broader landscape of cybersecurity.
SQL injection techniques
SQL injection remains one of the most prevalent vulnerabilities that ethical hackers encounter. By exploiting weaknesses in input validation, attackers can manipulate database queries and potentially gain unauthorized access to sensitive information. Understanding the techniques involved in SQL injection is crucial for any aspiring ethical hacker.
- Types of SQL Injection:
- In-band SQL Injection: This involves using the same channel to both launch the attack and gather results. It is the most straightforward method and commonly occurs within user input fields.
- Blind SQL Injection: In this scenario, attackers cannot see the output of their queries. Instead, they infer information based on the application’s responses, revealing systemic vulnerabilities.
- Out-of-Band SQL Injection: This technique uses different channels to retrieve data, often employing methods like DNS or HTTP for data extraction. It is less common but can be particularly devastating.
- Common Payloads:
- Tautology-Based Payloads: For example, using “OR ‘1’=’1′”. This injects a condition that is always true, allowing access to the database without proper authorization.
- Union-based queries: This technique combines the results of multiple SELECT statements. By injecting a UNION statement, attackers can retrieve data from other tables within the database.
- Detection and Mitigation: Implementing proper input validation, employing prepared statements, and using ORM (Object-Relational Mapping) frameworks can significantly reduce the risk of SQL injection attacks. It’s crucial to fortify systems against these vulnerabilities, as entering the world of unauthorized data access can be likened to opening a pandora’s box of potential damage.
In conclusion, mastering SQL injection techniques is essential for ethical hackers, enabling them not only to identify vulnerabilities but also to develop strategies to counteract these threats effectively.
Tools for database hacking
In the realm of ethical hacking, the right tools can make all the difference. Database hacking requires specialized software and utilities that enable ethical hackers to assess vulnerabilities, exploit weaknesses, and reinforce database security. Below are some of the critical tools covered in the course:
- SQLMap: This open-source tool automates the process of detecting and exploiting SQL injection vulnerabilities. It provides a simple interface for ethical hackers to conduct penetration tests, making it an indispensable asset in their toolkit.
- ZAP (Zed Attack Proxy): As an open-source web application security scanner, ZAP helps in identifying and mitigating vulnerabilities. Its intuitive GUI makes it accessible for beginners while providing powerful functionality for seasoned professionals.
- Burp Suite: This powerful web application security testing tool supports various functions including scanning for vulnerabilities, data manipulation, and intercepting communications to analyze requests and responses.
- Nessus: A comprehensive vulnerability scanning tool, Nessus assists in identifying security weaknesses across a broad range of systems, including databases. It offers detailed reports and recommended remediation steps.
- Shodan: Often referred to as “the search engine for the Internet of Things,” Shodan allows ethical hackers to gather intelligence on exposed devices and services, enabling them to identify potential targets in the database environment.
Understanding and employing these tools arms ethical hackers with the necessary resources to assess risks, exploit vulnerabilities, and recommend security enhancements effectively. Just as a master locksmith must have a complete set of tools to secure or breach doors, ethical hackers must know how to leverage these specialized tools to reinforce cybersecurity effectively.
Practical application of skills
One of the most compelling aspects of the “Ethical Hacking: Hacking Databases” course is its focus on practical application. Each module consists of practical exercises that reinforce theoretical knowledge, framing the course as not just an academic pursuit but as a concrete skill-building journey.
- Hands-On Labs: The curriculum is peppered with interactive labs that form a critical component of learning. These real-world exercises encourage students to implement their techniques immediately, preparing them for scenarios they may face in the workplace.
- Real-World Scenarios: By simulating various hacking situations, learners practice identifying vulnerabilities and exploiting them ethically acting in the capacity of an ethical hacker rather than simply reading protocols or methodologies.
- Project-Based Learning: Assignments are structured to reflect real hacking environments, ensuring participants know how to navigate the complexities of database systems. This approach is akin to training in a simulated aircraft before piloting a real one.
- Immediate Feedback: Instructors often provide insights into each exercise, allowing learners to refine their approaches and techniques continuously. The feedback loop fosters an atmosphere of learning and improvement.
Through these practical applications, students of the course gain not just knowledge but competence a crucial ingredient for success in the cybersecurity landscape, where hands-on experience is just as important as theoretical learning.
Exercises and hands-on experience
In the context of ethical hacking and database security, hands-on experience is imperative. The “Ethical Hacking: Hacking Databases” course by Stone River eLearning ensures students have ample opportunities to apply their knowledge through engaging exercises and practical assignments.
- Simulated Hacking Scenarios: Each chapter of the course ends with a hands-on exercise. This allows students to tackle simulated hacking challenges in a controlled environment, providing a platform for learning without the risk associated with real-world environments.
- Database Vulnerability Assessment: Participants conduct assessments on test databases by using the techniques they’ve learned, enabling them to identify vulnerabilities and suggest corrections effectively.
- Exploitation of Known Vulnerabilities: Students will have the chance to exploit common vulnerabilities, such as SQL injection or insecure configurations, and to understand the impact of these attacks on database integrity and security.
- Use of Tools: Practical exercises involve using tools such as SQLMap and ZAP to gather data, analyze potential threats, and fortify databases against future attacks. Participants can familiarize themselves with the nuances of each tool, ensuring they are prepared for real-world applications.
Through these rigorous exercises and hands-on experiences, students not only absorb information but also transform that knowledge into actionable skills an essential endeavor in today’s cybersecurity landscape.
Real-world scenarios
The practical application of theoretical knowledge is essential for aspiring cybersecurity professionals, and the “Ethical Hacking: Hacking Databases” course successfully incorporates real-world scenarios into its structure. By doing so, students can envision themselves in actual ethical hacking situations, effectively bridging the gap between learning and application.
- Case Studies: The course may include case studies of famous cybersecurity breaches that involved database exploitation. Delving into such instances illustrates the potential ramifications of inadequate security measures and highlights ethical principles in the field.
- Simulated Environments: Through the creation of simulated target databases, learners can practice identifying and exploiting vulnerabilities in a controlled setting, mimicking the experience of ethical hacking without the dangers associated with real-world attacks.
- Collaboration with Peers: Working in groups on certain assignments allows students to share insights, discuss strategies, and refine their techniques collaboratively much like working as a team in a professional cybersecurity setting.
- Response Protocols: Students learn how to react in the event of a potential security breach, developing skills to analyze threats and formulate appropriate responses a critical capability in real-world cybersecurity situations.
By integrating these real-world scenarios, the course empowers students to think critically and adaptively, transforming them into competent ethical hackers ready to tackle the cybersecurity challenges of today.
Certification and career opportunities
The “Ethical Hacking: Hacking Databases” course offers not only an educational pathway but also a clear route toward significant certification and career advancement in the cybersecurity domain. This dual focus on knowledge and practical application lays a strong foundation for rewarding professional opportunities.
- Certification Readiness: Upon successful completion of the course, participants will be well-prepared to pursue critical certifications in ethical hacking. Notable options include:
- EC-Council Certified Ethical Hacker (CEH): This globally recognized certification is a key credential for ethical hackers, validating expertise in penetration testing and security principles.
- CompTIA Security+: This foundational certification addresses core security concepts and practices, making it a valuable stepping stone for those new to cybersecurity.
- Diverse Career Paths: The skills gained through this course can lead to several career paths, including:
- Ethical Hacker: Professionals who conduct penetration tests to identify and mitigate vulnerabilities.
- Penetration Tester: Specialists focused on simulating attacks to evaluate security measures.
- Security Consultant: Advisors tasked with recommending security strategies and practices tailored to individual organizations.
- Database Security Engineer: Experts dedicated to protecting and managing the security of database systems.
- High Job Market Demand: The cybersecurity job landscape is abuzz with opportunity. As of now, there are over a million job openings globally for cybersecurity positions, with continuous growth projected over the coming years. The U.S. Bureau of Labor Statistics estimates a 32% increase in job availability by 2032, showcasing the high demand for trained professionals in this field.
- Salary Potential: Successful candidates can expect competitive salaries. Entry-level positions often yield six-figure salaries, reflecting the critical importance of cybersecurity roles in organizations today.
Thus, the course equips learners with the necessary skills and certification pathways to achieve meaningful careers in the cybersecurity industry, emphasizing the critical demand for their talents.
Industry-relevant certifications
In today’s cybersecurity landscape, attaining industry-relevant certifications is crucial for validating skills and enhancing employability. The “Ethical Hacking: Hacking Databases” course prepares participants for several key certifications that are highly regarded in the field:
- EC-Council Certified Ethical Hacker (CEH):
- Overview: This certification focuses on vulnerabilities and exploits, enabling certified ethical hackers to assess security systems through penetration testing and other ethical methods.
- Eligibility: Candidates typically require two years of experience in the Information Security domain and must pass a comprehensive exam.
- CompTIA Security+:
- Overview: A fundamental certification that emphasizes knowledge of security concepts, vulnerabilities, and incident management.
- Eligibility: While there’s no strict prerequisite, having a basic understanding of networks and IT fundamentals is advisable.
- Certified Information Systems Security Professional (CISSP):
- Overview: A more advanced certification suitable for those in managerial roles, the CISSP certifies an individual’s expertise in designing, implementing, and managing cybersecurity programs.
- Eligibility: Candidates must have at least five years of paid work experience in two or more of the eight domains covered in the CISSP topics.
- Certified Ethical Hacker (CEH) Practical:
- Overview: This certification validates proficiency in performing ethical hacking skills, focusing on practical application via hands-on testing.
- Eligibility: Completion of an official EC-Council CEH training and passing the exam.
These certifications not only enhance a professional profile but also illustrate a commitment to staying current with industry standards and practices, reinforcing the participant’s credibility in the eyes of employers and clients alike.
Job market demand in cybersecurity
The demand for cybersecurity talent is soaring, driven by an increase in cyberattacks, the rising complexity of security threats, and the critical need for robust data protection measures.
- Explosive Growth: According to the U.S. Bureau of Labor Statistics, job openings for information security analysts alone are projected to increase by 32% from 2022 to 2032. With ongoing developments in technology and a heightened focus on cybersecurity, this sector is expected to continue growing rapidly.
- Manpower Shortage: Currently, there are over a million job openings in the global cybersecurity landscape. The shortfall in skilled professionals emphasizes the significance of obtaining certifications and practical skills, providing an advantageous position for new entrants entering the field.
- Diverse Roles: The cybersecurity sector offers a wide array of roles, from ethical hackers and penetration testers to security specialists and consultants, allowing professionals to align their careers with their interests and skills.
- Competitive Salaries: Entry-level cybersecurity positions can offer salaries starting from six figures, depending on geography and company size. As professionals gain experience and specialized skills, potential earnings can increase significantly, reflecting the essential value of cybersecurity roles in protecting organizational assets.
Overall, the surge in job market demand underscores the critical need for certified professionals equipped with ethical hacking skills, making the “Ethical Hacking: Hacking Databases” course a valuable stepping stone for individuals looking to secure their place in this thriving field.
Course accessibility and format
The “Ethical Hacking: Hacking Databases” course provided by Stone River eLearning is notable for its accessibility and user-friendly format, designed to accommodate various learning styles and schedules.
- Online Format: As an online course, it allows students to access materials from anywhere and at any time. This flexibility is especially beneficial for individuals with busy lives, enabling them to learn at their own pace.
- Self-Paced Learning: Students can progress through the course modules at their own speed, allowing for deeper engagement with complex topics and the ability to revisit lectures as needed. This self-paced format is comparable to navigating a winding trail at one’s own speed, ensuring that learners feel comfortable and confident in their path to understanding.
- Multi-Device Access: The course is designed to be compatible with various devices, including computers, tablets, and smartphones. This ensures that students can continue their education regardless of their device preference, catering to a diverse range of technological ecosystems.
- Comprehensive Resource Library: The course encompasses not just video lectures but also supplemental materials such as guides, readings, and practical resources, ensuring that students have a comprehensive repository of materials at their fingertips.
In sum, the accessibility and format of the course emphasize student convenience and engagement, providing them the tools necessary to succeed in their cybersecurity education and enhancing their opportunities for skill acquisition.
Online learning flexibility
The online learning format of the “Ethical Hacking: Hacking Databases” course brings significant flexibility, allowing participants to manage their education on their terms. Here are four key areas where this flexibility shines:
- Personalized Pace: Whether a learner prefers a quick revision or a more laid-back study approach, the course accommodates personal preferences. Participants can choose how quickly or slowly they wish to progress through the materials, enabling a comfortable and enjoyable learning experience.
- Anytime, Anywhere Access: With 24/7 access to course materials, students can fit their studies into even the busiest schedules. This flexibility allows working professionals to learn outside work hours, making education more accessible.
- Adaptation for Various Learning Styles: Each learner brings a unique perspective and set of learning preferences to the table. The range of multimedia resources, live discussions, and hands-on exercises caters to different learning styles, ensuring that students absorb information effectively.
- Supportive Learning Environment: The online format does not sacrifice support and guidance. Learners can engage with fellow students and instructors through online forums, allowing for the exchange of knowledge and experience mirroring the collaboration often observed in traditional learning environments.
Overall, the flexibility inherent in the online learning format empowers participants to take control of their educational journey, balancing their studies with other responsibilities and personal goals.
Lifetime access benefits
One of the standout features of the “Ethical Hacking: Hacking Databases” course is its commitment to providing lifetime access to course materials. This benefit resonates particularly well in a field as dynamic as cybersecurity.
- Ongoing Education: With lifetime access, students can revisit course materials, refresh their knowledge, and stay updated with the latest trends and techniques in ethical hacking. This is akin to having a personal library of resources at one’s disposal, facilitating continuous professional development.
- Flexible Reviews: Learners can go back to specific modules or lectures whenever needed, making it easy to reinforce concepts that may require additional attention. This flexibility enhances the retention of vital information and skills learned throughout the course.
- Staying Current: Given the rapid evolution of technology and security threats, having unlimited access means participants can revisit materials to keep pace with changes in the field. Cybersecurity is not static, and continued exposure to fresh insights is crucial for successful professionals.
- Transitioning Between Roles: As professionals evolve in their careers, they may switch roles or focus areas within cybersecurity. The lifetime access allows users to refresh relevant skills or knowledge aligned with their career trajectory.
By providing lifetime access to the course materials, Stone River eLearning facilitates the long-term success and growth of its students, ensuring they remain equipped with the tools and insights necessary to excel in their careers.
Customer satisfaction and refund policy
Stone River eLearning prioritizes customer satisfaction, understanding that the ultimate goal is to provide meaningful educational experiences for its students. This commitment is evident in their customer-centric policies, including a transparent refund policy designed to instill confidence in learners.
- 30-Day Money-Back Guarantee: The course includes a refund policy that allows students to request a full refund within 30 days of enrollment if they are not satisfied with their experience. This no-questions-asked return approach underscores the company’s belief in the quality of its educational content.
- Trust and Confidence: Knowing they have the option to withdraw, learners can engage with the course without the fear of making an ill-fated investment. This peace of mind encourages exploration and growth while also signaling Stone River’s commitment to a positive learning environment.
- Focus on Quality: Implementing a customer satisfaction policy not only reassures students but also serves as an incentive for Stone River eLearning to maintain high content standards. The company’s success hinges on positive reviews and satisfied students, driving them to continually enhance their offerings.
- Encouraging Enrollment: The refund policy plays a pivotal role in attracting prospective students. With a risk-free learning proposition, individuals who might be hesitating to commit to a cybersecurity course are more likely to take the plunge, knowing an exit strategy is available should their expectations not be met.
In sum, the robust customer satisfaction and refund policy reflects Stone River eLearning’s dedication to cultivating a successful educational experience, reinforcing their core values centered around quality and learner engagement.
Money-back guarantee
Stone River eLearning stands firmly behind the quality of its course offerings, evidenced by its comprehensive money-back guarantee. This feature plays a crucial role in assuring prospective enrollees of their investment’s security.
- No-Risk Enrollment: The 30-day money-back guarantee assures students that if the course does not meet their expectations, they can request a full refund without facing any obstacles or questions. This policy, akin to a safety net, allows individuals to engage with the course with confidence.
- Encouragement to Explore: With the guarantee in place, learners can delve into the content freely, exploring various aspects of ethical hacking and database security without hesitation. This encourages a culture of experimentation and deeper understanding.
- Commitment to Quality: Stone River eLearning’s willingness to provide a money-back guarantee underscores its commitment to delivering high-quality and valuable educational experiences. The company invests in creating top-notch content so that enrollment translates into meaningful learning outcomes.
- Positive Reputation: Such customer-centric policies naturally foster positive word-of-mouth and enhance the company’s reputation in the education space. When students have positive experiences, they are more likely to share their feedback, contributing to a thriving academic community.
In essence, the money-back guarantee demonstrates Stone River eLearning’s confidence in its offerings while ensuring students feel secure in their decisions an essential element of fostering trust and satisfaction.
Student feedback and reviews
While independent student feedback and reviews specifically pertaining to “Ethical Hacking: Hacking Databases” by Stone River eLearning are not exhaustively documented, there are a number of insights gathered from the course descriptions and general program context that suggest positive reception among learners.
- Large Enrollment Figures: Stone River eLearning boasts over 1,200,000 students enrolled across various courses, indicating a significant interest and satisfaction within the student community. Large enrollment often signifies a course’s effectiveness and perceived value in the educational marketplace.
- Engagement Strategies: The hands-on approach involving practical exercises following each lecture appears highly valued by students. Engaging with real-world scenarios fosters a collaborative learning environment, indicative of a positive and effective experience.
- Variety of Course Offerings: The wide catalog of courses available signifies flexibility and opportunity for learners to explore different subjects. Such diverse offerings could reflect well on the overall satisfaction levels within the learning community.
- Peer-to-Peer Interaction: An active online community promotes collaboration, enabling students to exchange knowledge and experiences. This interactivity often leads to positive feedback, as community engagement enhances the overall learning experience.
While specific reviews and ratings from students may be beneficial, the evidence gathered suggests that Stone River eLearning has established a solid reputation within the online learning space. Prospective students can likely expect a positive educational experience rooted in comprehensive content and practical applications.
Additional resources and support
The “Ethical Hacking: Hacking Databases” course at Stone River eLearning is designed to equip students not only with essential skills but also with a wealth of additional resources and support that enhance the overall learning experience.
- Comprehensive Course Materials: In addition to video lectures, the course includes supplementary resources such as reading materials, guides, and checklists that reinforce learning. These resources serve as valuable references for students during and after course completion.
- Interactive Labs and Exercises: Students will engage in hands-on labs that complement the theoretical content, providing opportunities to practice techniques in simulated environments. This further solidifies understanding and enhances skill mastery.
- Mentorship and Support: Potential access to mentoring or forums where learners can interact with instructors and peers fosters a collaborative community. This kind of support is essential for students navigating complex topics and provides an avenue for seeking guidance.
- Networking Opportunities: Given the large student population at Stone River eLearning, individuals might find networking opportunities within the community. Collaborating with peers allows learners to share insights, collaborate on projects, and foster critical professional connections.
The breadth of additional resources and support surrounding the “Ethical Hacking: Hacking Databases” course ensures that students are well-equipped to succeed in their learning journey. This emphasis on comprehensive educational resources ultimately enhances students’ confidence and preparedness in tackling the challenges presented in the dynamic world of cybersecurity.
Course materials and supplementary content
The “Ethical Hacking: Hacking Databases” course encompasses a wide array of materials and supplementary content designed to create an enriching educational experience. Here’s a closer look at the key elements of the course structure:
- Core Curriculum:
- The course covers vital topics, including fundamental principles of ethical hacking, SQL injection techniques, and database security measures, ensuring a robust foundation in the subject area.
- Video Lectures:
- Packed with informative content, the presentations are complemented by visuals and real-world examples to illustrate concepts clearly. Learners can engage with these lectures at their convenience, helping to accommodate different learning styles.
- Supplementary Resources:
- Additional readings, tutorials, and reference materials support the core content, helping students explore topics more deeply. This variety aids in reinforcing comprehension and encourages critical thinking.
- Hands-On Labs:
- Practical exercises and lab activities allow learners to apply their knowledge and gain experience using tools such as SQLMap and ZAP. These simulations mirror real-world scenarios, preparing students for practical challenges in the cybersecurity field.
The organized presentation of course materials coupled with supplementary content ensures that learners have ample resources to support their studies, contributing to a comprehensive educational experience.
Community and networking opportunities
The importance of community and networking within the “Ethical Hacking: Hacking Databases” course cannot be overstated. Engaging with a larger network not only enriches the learning experience but also prepares students for their future careers in cybersecurity.
- Student Forums and Discussions:
- Platforms may be provided for learners to interact, share insights, and discuss important topics. This atmosphere fosters collaborative learning and allows students to seek answers and advice from fellow peers.
- Networking Events:
- Opportunities for virtual meetups or online workshops may occur, providing students with a chance to connect with industry professionals and fellow learners. Such interactions enable knowledge exchange and the building of relationships that can be beneficial for future career prospects.
- Peer Collaboration:
- Group projects integrated into the course encourage teamwork, promoting interpersonal skills vital for working in cybersecurity. Collaborating on assignments allows students to pool diverse perspectives and approaches to problem-solving.
- Online Communities:
- A large enrollment base, such as over 1,200,000 students, means that participants can tap into a wide variety of experiences and insights. Students can share tips and strategies, thus creating a rich learning environment that extends beyond the course itself.
In summary, the community and networking opportunities cultivated throughout the “Ethical Hacking: Hacking Databases” course empower learners to build connections and expand their professional networks, significantly enhancing their prospects in the dynamic cybersecurity landscape.
Conclusion on course value
In the rapidly evolving realm of cybersecurity, the “Ethical Hacking: Hacking Databases” course from Stone River eLearning stands out as a formidable resource for aspiring professionals. By combining comprehensive content, practical exercises, and a flexible learning environment, this course provides substantial value to individuals looking to secure a foothold in this booming industry.
With a commitment to ethical practices and an emphasis on real-world applications, learners are equipped with the tools necessary to address pressing cybersecurity challenges. The inclusion of industry-relevant certifications ensures that participants leave the course ready to pursue exciting career opportunities, all while embodying the skills needed to safeguard sensitive data across various platforms.
Overall, the course not only offers a pathway to certification and career success but also solidifies ethical hacking as a vital component of the cybersecurity landscape, ultimately fortifying the industry’s defenses against malicious threats.

Frequently Asked Questions:
Business Model Innovation:
Embrace the concept of a legitimate business! Our strategy revolves around organizing group buys where participants collectively share the costs. The pooled funds are used to purchase popular courses, which we then offer to individuals with limited financial resources. While the authors of these courses might have concerns, our clients appreciate the affordability and accessibility we provide.
The Legal Landscape:
The legality of our activities is a gray area. Although we don’t have explicit permission from the course authors to resell the material, there’s a technical nuance involved. The course authors did not outline specific restrictions on resale when the courses were purchased. This legal nuance presents both an opportunity for us and a benefit for those seeking affordable access.
Quality Assurance: Addressing the Core Issue
When it comes to quality, purchasing a course directly from the sale page ensures that all materials and resources are identical to those obtained through traditional channels.
However, we set ourselves apart by offering more than just personal research and resale. It’s important to understand that we are not the official providers of these courses, which means that certain premium services are not included in our offering:
- There are no scheduled coaching calls or sessions with the author.
- Access to the author’s private Facebook group or web portal is not available.
- Membership in the author’s private forum is not included.
- There is no direct email support from the author or their team.
We operate independently with the aim of making courses more affordable by excluding the additional services offered through official channels. We greatly appreciate your understanding of our unique approach.
Be the first to review “Ethical Hacking: Hacking Databases with Stone River eLearning” Cancel reply
You must be logged in to post a review.

 Photoshop Roundtrip in Adobe Lightroom Classic with Jared Platt
Photoshop Roundtrip in Adobe Lightroom Classic with Jared Platt 









Reviews
There are no reviews yet.