Ethical Hacking: Recon and Footprinting with Stone River eLearning
6,00 $
Download Ethical Hacking: Ethical Hacking: Recon and Footprinting with Stone River eLearning, check content proof here:
Ethical Hacking: Stone River eLearning’s Recon and Footprinting
In the current digital environment, when security lapses and online attacks are rampant, ethical hacking becomes a crucial activity for both individuals and companies trying to protect their online spaces. With a focus on the critical phases of reconnaissance and footprinting, Stone River eLearning’s course “Ethical Hacking: Recon and Footprinting” offers a thorough examination of the fundamental components of ethical hacking.
This course serves to demystify the subject of cybersecurity by providing students with both academic knowledge and practical abilities. This allows learners to move into jobs that are in high demand and may lead to rewarding employment.
Ethical hacking is more than simply a skill set; it’s a proactive approach to cybersecurity in which obtaining information is used to strengthen defenses rather than compromise them. Welcomed into an environment where they may investigate the methods hackers use, students can learn how to identify weaknesses and how to protect themselves.
During the course, students embark on a life-changing experience that includes technological expertise as well as ethical thinking—a crucial component in this field where abuse may have dangerous consequences. This course provides a means of acquiring information, developing skills, and comprehending ethics via hands-on activities and professional supervision.
summary of the course material
A wide range of information is covered in the “Ethical Hacking: Recon and Footprinting” course, which is intended to help both inexperienced and seasoned IT workers improve their ethical hacking abilities. The course covers important subjects like Email and Website Footprinting, Nmap, and Metasploit in an interesting way that’s similar to piecing together a mystery novel. Every subject offers insightful information and the resources needed to successfully traverse the ethical hacking landscape.
Here is a sneak peek at the course contents:
- Website and Email Footprinting: Knowing how to retrieve important data from websites that are openly accessible.
- Gaining the ability to investigate open ports and services on target systems using Port Inspection with Netstat.
- Mastering the use of Nmap and Metasploit: These are two extremely potent tools for penetration testing and network analysis.
- Maltego: Acquiring proficiency in sophisticated data mining instruments to illustrate connections across diverse entities.
- Learn about DNS queries and domain registration information with Whois and Nslookup.
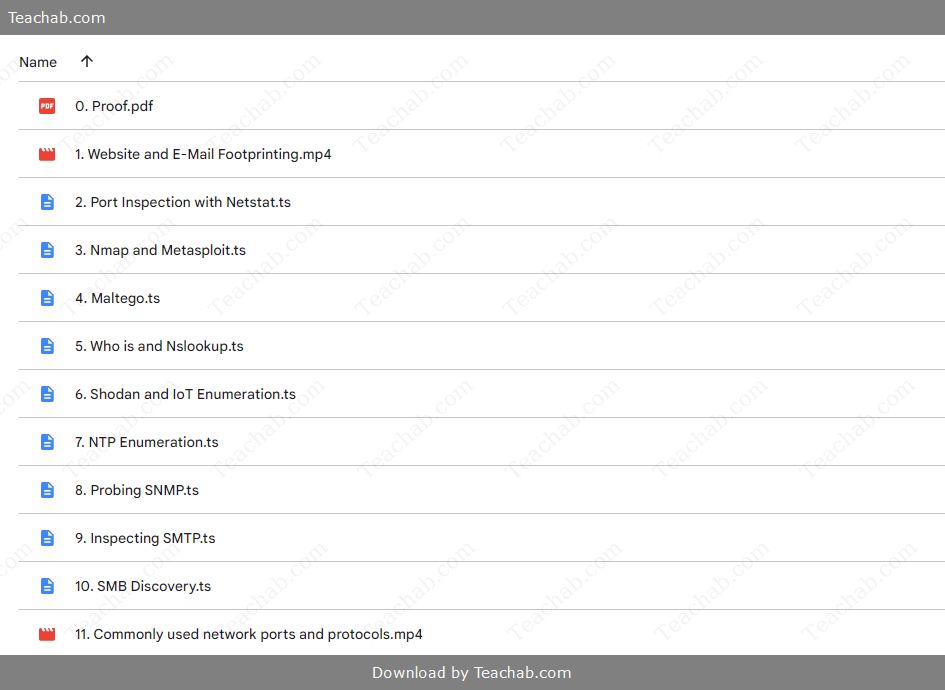
Table: Overview of the Course
| Module | Duration |
| Website and Email Footprinting | 04:11 |
| Port Inspection with Netstat | 03:03 |
| Nmap and Metasploit | 02:32 |
| Maltego | 05:24 |
| Whois and Nslookup | 03:06 |
| Shodan and IoT Enumeration | 03:22 |
| NTP Enumeration | 01:16 |
| Probing SNMP | 02:25 |
| Inspecting SMTP | 00:35 |
| SMB Discovery | 02:04 |
| Commonly Used Network Ports | 14:06 |
Every one of these classes provides essential information and useful perspectives, creating a solid base on which students may expand. The course is made with practical learning and simple navigation in mind, preparing students for success in their ethical hacking endeavors.
An in-depth analysis of the course modules
The course is carefully designed so that students gain practical knowledge and abilities throughout time. Learners explore the importance of obtaining vital information about possible targets without using invasive methods, beginning with website and email footprinting. This stage teaches them how to get relevant information about their objectives by using easily accessible resources like search engines and registry information.
The next section of the course, Port Inspection using Netstat, teaches students how to examine different network ports in order to identify vulnerabilities and services. They get the capacity to precisely evaluate security postures and identify abnormalities through hands-on training.
The second section covers the use of powerful tools like Nmap and Metasploit, where students may learn how to run network scans and find vulnerabilities on various devices. By participating in situations that mimic real-world difficulties, students gain confidence in their technical skills.
Furthermore, participants are given advanced skills through courses like Shodan, IoT Enumeration, and Maltego. Here, students study the visualization of intricate linkages and vulnerabilities in networked devices, improving their analytical abilities and cybersecurity strategy. By looking at a variety of protocols and learning how to probe networks successfully, the training’s conclusion expands the participants’ comprehension of potential vulnerabilities in cybersecurity frameworks.
Major Pointers for Each Module:
- Module 1: Outlines key ideas for obtaining intelligence.
- Module 2: Employs tools for enumerating services and port scanning.
- Module 3 teaches students how to use a variety of techniques to find vulnerabilities.
- Module 4: Offers a comprehension of interconnected systems and techniques for in-depth reconnaissance.
By participating in these course modules, students may gain a comprehensive understanding of ethical hacking. This methodical yet adaptable approach accommodates a variety of learning styles, making it suitable for a broad range of users, from total beginners to IT experts looking to expand their knowledge.
Important learning goals and results
The clearly stated learning goals of the “Ethical Hacking: Recon and Footprinting” course provide its foundation. With a clear design, the goals expose important layers of information as students move through the course, much like an onion.
- Reconnaissance: The importance of reconnaissance in ethical hacking will be understood by the students. using the emphasis on effective data collection using non-invasive means, pupils get an understanding of the fragility and sensitivity of the information at hand.
- Practical Application: Through practical tasks that let students put what they’ve learned into theoretical contexts, each module places a strong emphasis on application. This feedback loop encourages a do-it-yourself attitude in cybersecurity procedures by improving recall and confidence in the approaches.
- Certification Preparation: Students may efficiently prepare for tests such as the Certified Ethical Hacker (CEH) thanks to the curriculum’s direct alignment with industry certification standards. The course content equips students with the necessary information to succeed in certification pursuits and bolsters their professional reputation.
- Career Readiness: This course prepares students for entry-level cybersecurity positions. Their employment chances are greatly enhanced by the skills they have gained during the curriculum; many students have expressed increased confidence and readiness for obstacles associated to the business.
By integrating theory with hands-on practice and matching learning goals with industry norms, the course puts students at the forefront of professional needs and regulatory expectations. The essential skills learned in this course are crucial for navigating the cybersecurity landscape, regardless of the students’ professional goals.
Tools and methods discussed
Knowledge of cutting-edge tools and methods is crucial when it comes to ethical hacking. The training offers a demanding experience with several programs that form the basis of several hacking schemes.
- Maltego: This tool makes it possible to delve deeply into the relationship mapping between individuals, groups, and technology. This is crucial for identifying links that can be concealed and provide security problems.
- Nmap: A mainstay of the cybersecurity toolbox, Nmap lets users do thorough scans and makes it simple to find active hosts, open ports, and services that are currently operating.
- Metasploit: Widely regarded as the hacker’s friend, this framework speeds up penetration testing by making it easier to find flaws and test cybersecurity measures.
- Netstat: This command-line tool is essential for comprehending network traffic as it helps with troubleshooting and connection verification.
Table: Comparing Tools
| Tool Name | Primary Function | Use Case Example |
| Maltego | Informational data mining | Mapping relationships between entities |
| Nmap | Network discovery and security auditing | Identifying active hosts and their open ports |
| Metasploit | Penetration testing framework | Exploiting vulnerabilities to assess security defenses |
| Netstat | Network statistics | Monitoring server connections to ensure security |
These resources are essential for anybody interested in a career in ethical hacking as they represent the industry’s best practices. Practical activities complement each tool, ensuring that trainees understand not just how to use the tools but also the tactical attitude that underpins their usage.
Course arrangement
“Ethical Hacking: Recon and Footprinting” is purposefully structured to provide a thorough educational experience. By segmenting the content into discrete learning units, students may progressively expand their understanding without feeling overburdened.
Important components of the course design consist of:
- An Introduction to Ethical Hacking lays forth the foundational concepts, vocabulary, and history of ethical hacking.
- Focused Learning Pathways: Each lesson walks students through the intricacies of reconnaissance and footprinting by highlighting a crucial component of each.
- Practical Components: At the conclusion of each module, learners are encouraged to use newly acquired abilities through practical tasks that turn theory into reality.
Over the course of around four hours and eighteen minutes, students take a somewhat intensive yet thorough deep dive into the field of ethical hacking at every turn. Through interactive activities, this framework maintains the course’s robustness and accessibility, accommodating students of different learning paces and keeping them engaged.
Time and structure
It is essential for the potential student to comprehend the time commitment required. Given that the course lasts for around four hours and eighteen minutes, anyone who must juggle job, school, or other obligations may commit to it.
Students benefit from an online, self-paced style that encourages convenience and lets them go at their own pace. The course allows for scheduling flexibility, whether it’s through a brief refresher at lunch breaks or a late-night study session.
Additionally, the course makes use of a variety of multimedia forms, including video lectures, case studies, and hands-on evaluations, to provide students with rich learning experiences that accommodate different learning preferences. The course aims to enhance learning retention by maintaining relatability and interest through captivating images and real-world events.
Lecture subjects and scheduling
Every lesson in the course is carefully scheduled to give students an effective way to grasp the fundamentals of ethical hacking reconnaissance and footprinting. The particular lecture subjects and the time allotted for them are listed below:
| Lecture Topic | Time Allocation |
| Website and E-Mail Footprinting | 04:11 |
| Port Inspection with Netstat | 03:03 |
| Nmap and Metasploit | 02:32 |
| Maltego | 05:24 |
| Whois and Nslookup | 03:06 |
| Shodan and IoT Enumeration | 03:22 |
| NTP Enumeration | 01:16 |
| Probing SNMP | 02:25 |
| Inspecting SMTP | 00:35 |
| SMB Discovery | 02:04 |
| Commonly Used Network Ports and Protocols | 14:06 |
This well-organized design enhances the learning process of the course as a whole, allowing students to delve deeply into each subject while preserving coherence and clarity throughout their academic careers.
Exercises and applications that are practical
The “Ethical Hacking: Recon and Footprinting” course relies heavily on practical activities. Practical exercises are included at the end of each chapter to help reinforce the principles covered in a real-world setting.
These tasks successfully simulate real-world situations where students may use their newly acquired ethical hacking abilities. Students’ learning experience is reinforced when they are asked to run network scans in a controlled environment after learning about Nmap. This allows them to find open ports and services on designated targets.
Furthermore, students can interact directly with the topics covered through exercises like examining SMTP traffic or doing a footprinting experiment on a fictitious website. These real-world examples guarantee that students can successfully apply tactics in addition to understanding theories.
The course prepares students for a variety of industrial difficulties they may face in their future professions by bridging the theoretical and practice gaps. This practical method encourages experimentation, creativity, and self-assurance while taking on cybersecurity-related activities.
Quality of instruction
“Ethical Hacking: Recon and Footprinting” is a highly instructive course that demonstrates Stone River eLearning’s dedication to providing worthwhile learning opportunities. The course is created with the student in mind, with a focus on practical application, engagement, and clarity—all of which are essential for grasping difficult ethical hacking concepts.
In order to accommodate various learning types, the curriculum combines real-world scenarios, visual features, and a variety of teaching techniques. With an emphasis on improving understanding and retention, students are guided through the nuances of ethical hacking through the use of interactive materials, video lectures, and demonstrations.
Furthermore, during the course, students may assess their learning thanks to the structured feedback mechanism that has been included. Positive reinforcement in the form of practical evaluations aids in the consolidation of acquired concepts and clarifies any areas that could need further attention.
With well thought-out teaching components, the course guarantees a top-notch learning experience, enabling students to successfully understand even the most difficult ethical hacking subjects.
Qualifications and experience of the instructor
The creator of the course is Stone River eLearning, a company well-known for its dedication to IT education across a broad spectrum of IT disciplines. While particulars about individual teachers are not provided, Stone River eLearning has a sizable student body of more than 3.2 million, which suggests that it has a solid reputation for providing demanding course materials.
Furthermore, the curriculum of the course is in line with credentials like the Certified Ethical Hacker (CEH), which helps students stand out in the job market. Well-crafted, industry-compliant curricula created by certified teachers are crucial markers of a successful course design.
This depth of knowledge and the institution’s commitment to high standards of instruction are advantageous to learners. Students may choose a course that will give them more confidence in their investment in developing their abilities because it is based on tried-and-true teaching methods supported by experienced experts.
Methods of instruction
The “Ethical Hacking: Recon and Footprinting” course employs a varied teaching technique that aims to provide students with a thorough educational experience. It balances theoretical instruction with real-world applications to make sure students understand the material and can use it successfully.
- Interactive Lectures: Classes are designed around interesting video lectures that concisely and interestingly cover the key ideas. This method is similar to enrolling in an online course where knowledgeable teachers tell engrossing stories about ethical hacking.
- Hands-on Labs: Practical exercises that encourage students to actively participate in implementing methods supplement each subject. This experiential approach facilitates information retention and motivates students to engage with real-world situations.
- Self-Paced Learning: Students are able to learn at their own speed due to the course’s flexible framework. This factor greatly improves the overall learning experience by allowing for varying learning rates and timetables.
- Evaluation and Comments: After every lesson, learners are given progress tests to make sure they understand the fundamentals before moving on. Regular evaluation and feedback promote retention and draw attention to areas that still require improvement.
Through the use of this dynamic teaching style, Stone River eLearning fosters a comprehensive learning environment. Together, these elements foster learners who are not just informed but also competent in using their talents in the field of ethical hacking.
Availability of resources
A multitude of materials and tools designed to improve participants’ learning experience are promised in the “Ethical Hacking: Recon and Footprinting” course. Easy access to a wealth of course materials, such as downloadable materials, video lectures, and useful tools, is provided to students, giving them a broad range of information to choose from.
- Course Materials: To enhance their learning, participants have access to a variety of instructional resources. These consist of comprehensive lecture notes, summaries of important ideas, and connections to other resources for reading.
- Supplementary Tools: Throughout the course, students are exposed to industry-standard tools like Nmap, Metasploit, and Maltego. Success in the field of ethical hacking depends on your ability to comprehend and make use of these resources.
- Community assistance Options: The Stone River eLearning community itself offers networking options between fellow learners, while the characteristics of the platform may determine the type of community assistance offered. These kinds of networks can produce priceless experiences and shared information.
- Flexibility in Access: Having lifetime access to the course materials is a great benefit. This feature improves long-term retention by enabling students to review instructional material whenever needed.
With a wealth of resources at their disposal and ongoing assistance, students are prepared to take on obstacles in the field of ethical hacking.
Availability of additional resources
Supplementary materials give students more tools to support their comprehension and practical skills, enriching the learning experience. The course “Ethical Hacking: Recon and Footprinting” takes a comprehensive stance on resource accessibility.
Important supplemental resources consist of:
- Reading List: eBooks and articles on important subjects related to ethical hacking and market developments.
- Realistic Lab Environments: By putting students in role-playing situations that mimic actual security issues, proactive skill application is made possible.
- Videos: Additional educational films that restate important ideas discussed in lectures in a way that facilitates understanding.
In the end, these tools enhance the learning process. Students’ comprehension of the cybersecurity landscape may be expanded by delving deeper into subjects and keeping up with new developments.
Features for the community and assistance
Support from the community becomes apparent as a crucial part of the ethical hacking learning process. In addition to offering a venue for knowledge sharing and project collaboration, an active community improves the educational experience for students.
Peer interactions are facilitated via Stone River eLearning, which enables students to establish connections, share ideas, and ask for help. Students can ask questions and have conversations about the course material in discussion boards and with direct teacher access, however particular community support tools may differ.
Networking with like-minded people also promotes teamwork and offers a variety of viewpoints on cybersecurity issues. By exchanging materials, ideas, and best practices, students may build a rich body of knowledge that encourages lifelong learning.
The focus on the community creates an atmosphere that is ideal for inquiry and intellectual curiosity. It helps learners to maintain connections and engagement across the course of their education.
Opportunities for career progression
In addition to providing participants with technical skills, the “Ethical Hacking: Recon and Footprinting” course offers up a wide range of professional progression options in the rapidly growing field of cybersecurity. The need for proficient ethical hackers is only going to get stronger as more and more companies realize how important it is to have strong cybersecurity safeguards.
- Specialization and Certification: Students that get ethical hacking training are more equipped to pass certification tests, such the Certified Ethical Hacker (CEH), improving their chances of finding employment. Obtaining certification adds a great deal of credibility in the industry.
- Diverse Career Pathways: Students can successfully move from entry-level jobs into a variety of specialized cybersecurity professions, such as penetration tester, security analyst, and cybersecurity consultant. Professionals that specialize in recon and footprinting are better equipped to undertake comprehensive security evaluations.
- Opportunities for Freelance: Opportunities for freelancing are part of an accessible professional track. Ethical hackers frequently operate as independent contractors, which may offer competitive pay, a variety of jobs, and flexible work schedules without the limitations of regular employment.
- Growth Sector: It is anticipated that the cybersecurity sector will keep growing, offering constant chances for innovation and technical breakthroughs. In order to stay current and flexible in this industry, professionals must keep up with the latest developments in cyber risks.
Because the course is transformational, students will be able to successfully use their talents in a flourishing employment market. The frameworks created by the program support long-term advancement in the cybersecurity industry.
Perspectives on the cybersecurity job market
The increasing prevalence of cyber dangers has resulted in an unprecedented demand for cybersecurity specialists, particularly ethical hackers. Many career possibilities are created by the changing cyber landscape, which reflects the high demand in the business.
- Demand Boom: According to surveys, there is a concerning global lack of skilled cybersecurity workers, with millions of open opportunities. Recognizing the value of cybersecurity positions for legacy and operational continuity, organizations are investing more and more in these positions.
- Lucrative Salary: Due to the specialized knowledge needed and the vital nature of the work, ethical hacking employment frequently pay well. Cybersecurity entry-level positions may pay six figures, and with growing abilities and experience comes more opportunities for advancement.
- Future Sustainability: Ethical hackers will continue to be important due to the blurring borders between cybersecurity and future technologies. Continuously learning professionals will prosper when new technologies emerge and creative solutions require the abilities they learned in this course.
With the ever-changing field of cybersecurity, those with experience in recon and footprinting will have a clear advantage in their future jobs.
Benefits of certification and career pathways
Upon completion of the “Ethical Hacking: Recon and Footprinting” course, one may easily get industry certifications that are highly valued and improve one’s chances of landing a cybersecurity job.
- Direct Certification Preparation: The course is carefully crafted to assist students in getting ready for certifications that are recognized in the field, such as CompTIA Security+ and the EC-Council Certified Ethical Hacker (CEH). Obtaining these credentials increases a person’s employability by validating their proficiency.
- Essential Skill Development: A proficient ethical hacker’s toolkit should include critical abilities like executing efficient reconnaissance and footprinting. The hands-on learning opportunities provided by the course equip students for a variety of professional obstacles.
- Competitive Advantage: After completing this introductory course, candidates frequently stand out in both interviews and job applications. The program’s knowledge and abilities make for impressive resumes, especially when supported by certificates.
- Opportunities for Networking: Students can use the contacts they make in the course to further their careers by competing for in-demand positions in an area that is changing quickly.
The importance of taking the “Ethical Hacking: Recon and Footprinting” course as a necessary first step toward a lucrative cybersecurity profession is highlighted by the combination of these elements.
Evaluations and rankings
Participants in the “Ethical Hacking: Recon and Footprinting” course have left positive evaluations, praising the usefulness of the materials, the high caliber of training, and the educational value.
- High Ratings: The course has an overall satisfaction rating of 4.4 stars across several platforms, indicating that students are generally satisfied. The instructional materials’ high degree of involvement and clarity have received a lot of acclaim, which greatly improves the learning process.
- Effective Instruction: The teacher’s approach to teaching has been praised for its ability to deconstruct difficult ideas. Reviews from students typically highlight the instructor’s capacity to offer perspectives that connect with students and simplify complex concepts.
- Applicability of Skills: Evaluations also emphasize how much of a practical application the course provides, assisting students in gaining a practical grasp of ethical hacking methods and how to apply them in real-world situations.
- Industry Relevance: Students frequently mention how the course material relates to real-world employment prospects in the rapidly expanding cybersecurity industry, offering them the knowledge and skills they need to start new professional endeavors.
The “Ethical Hacking: Recon and Footprinting” course has received extremely good reviews, making it stand out as a top educational option for anybody looking to enter or advance in the cybersecurity field.
Testimonials and comments from students
The course’s substance and quality are strongly affirmed by the feedback given by students. Testimonials emphasize a number of elements that add to the course’s attractiveness, such as the instructors’ credentials, the participatory aspect of the activities, and the depth of the subject.
- Better Knowledge Base: A lot of students say the course has made a big difference in how well they grasp the fundamentals of ethical hacking. Responses show that the material offered is useful and immediately relevant to the cybersecurity difficulties they confront.
- Sharing Success Stories: After finishing the course, several students have reported successfully landing entry-level cybersecurity positions. Positive testimonies highlight how well-prepared they were for interviews and their first jobs in the business through hands-on training.
- Good Community Atmosphere: Participants frequently speak about the encouraging atmosphere that the Stone River eLearning community provides, which enables them to interact with others, have conversations, and exchange ideas, all of which enhance their learning process.
- Boost Your Confidence: Several student testimonies highlight how the course has empowered them, giving them the knowledge and abilities necessary to continue their professions in ethical hacking with renewed assurance.
These encouraging stories enhance the standing of the “Ethical Hacking: Recon and Footprinting” course, which makes it an appealing choice for those who want to work in cybersecurity.
Comparing this course to others on ethical hacking
Even if the “Ethical Hacking: Recon and Footprinting” course is unique in a number of ways, it’s important to comprehend how ethical hacking education as a whole is shaped by it. Upon comparison with other well-known courses, a number of significant distinctions and parallels surface.
- Content Depth: While other courses may cover more advanced techniques or more areas under ethical hacking, the Stone River course stays focused on fundamental skills like recon and footprinting, in contrast to some of its peers on platforms like Pluralsight.
- Interactive Learning: Stone River’s focus on real-world activities makes it possible for students to have a hands-on experience that is frequently more restricted on other platforms where academic knowledge may take precedence over real-world applications. This could be a deciding factor for students who want to use their talents right away.
- Instructor Engagement: One noteworthy feature of the Stone River course that makes it possibly more interesting to people who are concerned with help and direction from competent experts throughout their learning journey is feedback regarding the quality of the instructors.
- Certification Alignment: While certification preparation is emphasized on both Stone River and other platforms, Stone River aligns directly with credentials like the Certified Ethical Hacker (CEH), which attracts students who understand the value of certifications in advancing their careers.
In contrast, the “Ethical Hacking: Recon and Footprinting” course includes a number of advantages that support certain learning goals and help it to stay ahead of the competition in the field of ethical hacking instruction.
Final thoughts and suggestions
The Stone River eLearning course “Ethical Hacking: Recon and Footprinting” offers a comprehensive educational experience that develops the fundamental information and useful skills required for success in the cybersecurity industry. For those who are new to ethical hacking as well as seasoned IT professionals looking to advance their skills, this course proves to be a useful resource.
Suggestions for Potential Students:
- Accept Hands-On Training: Give your all during practical activities to ensure you thoroughly grasp the ideas covered in the course.
- Connect with the Community: Make the most of the networking possibilities that your fellow students provide you. They can help you advance both professionally and academically.
- Go for Certifications: Apply the knowledge you’ve learned in this course to be ready for industry-recognized certifications that will boost your credibility and employability in the business.
- Keep Up to Date: Because cybersecurity is a field that is always changing, look for new materials and resources that cover the latest methods and trends.
Students may strategically position themselves for success, preparedness, and flexibility within the rapidly expanding and dynamic cybersecurity field by actively following these tips.
Overall course effectiveness
Positive student comments, proof of understanding of difficult ideas, and the course’s practical focus—which gives students a clear path into cybersecurity careers—have all proved the course’s overall efficacy. Students that apply the information and abilities they have learned in this course to the field of ethical hacking discover rewarding career paths, increased employability, and support from the community.
Appropriateness of target audience
The course “Ethical Hacking: Recon and Footprinting” is intended for individuals who want to increase their knowledge, IT specialists who want to become certified, and aspiring cybersecurity professionals. The course is accessible to everyone who is dedicated to pursuing a career in ethical hacking, thanks to its flexibility and comprehensive curriculum, which accommodate individuals from a variety of backgrounds.

Frequently Asked Questions:
Business Model Innovation:
Embrace the concept of a legitimate business! Our strategy revolves around organizing group buys where participants collectively share the costs. The pooled funds are used to purchase popular courses, which we then offer to individuals with limited financial resources. While the authors of these courses might have concerns, our clients appreciate the affordability and accessibility we provide.
The Legal Landscape:
The legality of our activities is a gray area. Although we don’t have explicit permission from the course authors to resell the material, there’s a technical nuance involved. The course authors did not outline specific restrictions on resale when the courses were purchased. This legal nuance presents both an opportunity for us and a benefit for those seeking affordable access.
Quality Assurance: Addressing the Core Issue
When it comes to quality, purchasing a course directly from the sale page ensures that all materials and resources are identical to those obtained through traditional channels.
However, we set ourselves apart by offering more than just personal research and resale. It’s important to understand that we are not the official providers of these courses, which means that certain premium services are not included in our offering:
- There are no scheduled coaching calls or sessions with the author.
- Access to the author’s private Facebook group or web portal is not available.
- Membership in the author’s private forum is not included.
- There is no direct email support from the author or their team.
We operate independently with the aim of making courses more affordable by excluding the additional services offered through official channels. We greatly appreciate your understanding of our unique approach.
Be the first to review “Ethical Hacking: Recon and Footprinting with Stone River eLearning” Cancel reply
You must be logged in to post a review.
Related products
Technology
Technology











Reviews
There are no reviews yet.