GMBs Verification 2024
5,00 $
You may check content proof of “GMBs Verification 2024” below:
GBMS Verification 2024
In today’s fast-paced digital landscape, the importance of verification systems cannot be overstated, especially within Global Business Management Systems (GBMS). As businesses continue to evolve and adapt, so do the challenges associated with ensuring the credibility and reliability of their processes and outputs.
GBMS verification in 2024 emerges as an essential aspect of maintaining user trust, enhancing the integrity of data, and solidifying a company’s reputation amidst fierce competition. As organizations increasingly rely on data-driven decisions, the verification process aligns closely with relevant technologies, ethical standards, and the ever-growing demand for transparency.
As we venture into this article, we will explore the multiple facets of GBMS verification. We’ll address not only its significance but also the processes involved, the challenges faced, and the advanced technologies that play a crucial role in improving verification systems. Furthermore, we’ll provide practical guidance on best practices for implementation and evaluate the emerging trends that will shape the landscape of GBMS verification in the years to come. Thus, our exploration of GBMS verification will encompass an understanding of its importance, followed by detailed analyses of various elements such as user trust, business reputation, verification processes, innovative technologies, and future predictions.
Importance of GBMS Verification
Verification is the bedrock upon which business credibility is built. In the world of GBMS, the significance of verification cannot be overlooked as it directly influences user trust and data integrity. Imagine a sturdy bridge that connects two pieces of land; if the foundation begins to crumble, the structure becomes susceptible to collapse. Similarly, without robust verification processes, businesses risk losing trust and credibility in the eyes of their users.
Key indicators showcase the importance of verification:
| Aspect | Description |
| **User Trust** | Effective verification instills confidence in users, leading to engagement and loyalty. |
| **Data Integrity** | Accurate verification ensures data quality, enabling informed decision-making and reducing error rates. |
| **Competitive Advantage** | Verified systems stand out in a crowded market, attracting users who seek reliable and trustworthy solutions. |
According to a 2022 Deloitte survey, over 75% of users would consider a business that has a verified profile as more trustworthy. This emotional connection translates into tangible business outcomes, where customer loyalty is closely linked to their perception of a company’s reliability and transparency.
Moreover, as GBMS integrates advanced technologies, users increasingly expect high standards in verification processes. This creates a scenario where businesses must adapt to remain innovative while ensuring the accuracy and legitimacy of their operational practices. A company that prioritizes verification is not merely complying with regulations but is also fostering an environment that values user satisfaction and long-term partnerships.
In summary, GBMS verification serves as a crucial conduit for building trust, ensuring data integrity, and maintaining a competitive edge in the dynamic world of business management. The interplay between user expectations and technological evolution makes verification not just beneficial but essential for sustainable success.
User Trust in GBMS Verification
User trust is a pillar of any successful business venture, particularly within the context of GBMS verification. In the rapidly evolving landscape of digital interactions, trust is what makes or breaks relationships in the business world. Trust emerges not only from the quality of services offered but also from the ability to verify those services as reliable and effective. Think of user trust as the sunshine that nurtures a blooming flower; without it, growth and success remain stunted.
The relationship between verification and user trust can be illustrated as follows:
| Trust Factor | Role of Verification |
| **Transparency** | Users seek clarity on how services function; verification communicates honesty. |
| **Accuracy** | Verified systems ensure accuracy in predictions and results, resonating trust. |
| **Consistency** | Ongoing verification helps maintain consistent user experiences, enhancing reliability. |
| **Accountability** | Verification fosters a sense of accountability, as users feel secure interacting with legitimate services. |
A study by Accenture found that 83% of consumers expressed a desire for more transparency around data usage and verification in businesses they interact with. This statistic underscores the need for organizations to be proactive in communicating their verification processes and protocols.
Additionally, the integration of data verification technologies can further bridge the trust gap. Users want to know that their data is not just secured but is also validated. As digital transactions escalate, so does the urgency for businesses to adopt mechanisms that cultivate trust through verification. Moreover, in an era where misinformation runs rampant, users are increasingly discerning and reliant on validated sources.
In essence, user trust within the sphere of GBMS verification is paramount. It depends significantly on the transparency, accuracy, and reliability of the verification processes implemented by businesses. By prioritizing these elements, organizations can cultivate an environment ripe for fostering trusting relationships with their users, ultimately leading to sustained growth and loyalty.
Impact of Verification on Business Reputation
In the digital age, a company’s reputation can significantly impact its overall success. The process of GBMS verification plays a vital role in shaping and enhancing a company’s reputation through various channels and interactions. Consider a ship navigating through turbulent waters; the strength of its hull will determine whether it can weather the storm unscathed. Similarly, the resilience of a company’s reputation depends on the soundness of its verification practices.
- Trust Creation: Verified businesses are viewed as more credible, resulting in higher customer loyalty. When customers see that a company is verified, they are more inclined to engage with its products or services, perceiving them as quality offerings.
- Enhanced Visibility: Verification often leads to greater visibility in search engines and online platforms, effectively increasing the chances of attracting potential clients. Verified profiles frequently appear higher in search results, providing a competitive advantage.
- Improved Customer Engagement: A verified business can interact and engage effectively with its audience, responding to reviews and inquiries promptly. This interaction is critical in building a positive reputation and instilling confidence in potential customers.
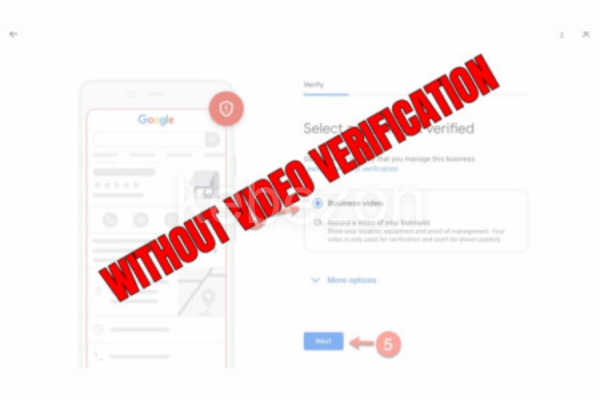
Process of Verifying GBMS Accounts
The verification process for Global Business Management Systems (GBMS) accounts involves several critical steps that establish credibility and accuracy for users. Generally, the undertaking of this process requires businesses to navigate through stages that confirm their legitimacy in the marketplace.
- Creating an Account: The preliminary step includes establishing a profile on the GBMS platform, including vital information like the business name and address.
- Providing Documentation: Companies must furnish documentation that proves their authenticity, such as business licenses or tax identification.
- Verification Methods:
- Phone Verification: Automated calls provide a verification code that needs to be entered.
- Mail Verification: A postcard is sent to the registered business address with a code that must be confirmed.
- Email Verification: A verification link is emailed, requiring confirmation.
- Approval and Confirmation: Once verification is completed, businesses receive confirmation of their verified status, typically within a few days.
- Regular Updates and Monitoring: Companies are encouraged to keep their information up to date, responding to new reviews promptly to maintain active engagement.
In summary, the verification process for GBMS accounts is not merely a formality; it is a critical component that enhances the organization’s ability to engage meaningfully with its audience. Organizations that follow these steps diligently can establish credibility, engender trust, and solidify their reputation successfully.
Step-by-Step Guide for Verification
To facilitate the verification of Global Business Management System (GBMS) accounts, organizations should follow a systematic step-by-step guide. This approach ensures that the process is transparent, efficient, and timely.
- Sign In to Your GBMS Account: Begin by navigating to the relevant platform and signing in using your business credentials.
- Locate the Verification Section: Within the dashboard, find the verification section, often marked with a “Verify Now” option.
- Choose Verification Method:
- Mail: Anticipate receiving a postcard from the platform with a verification code.
- Phone: Opt for a phone call or message to receive your code.
- Email: Alternatively, verify via a link sent to your registered email.
- Complete Verification Instructions:
- For mail, enter the code from the postcard into the verification field.
- For phone or email, type the received code as instructed.
- Post-Verification: After successful verification, review the account details to ensure all information is completed and accurate.
- Review and Update: Continually check and update the profile as necessary to reflect any changes promptly.
By adopting this structured guide, organizations can navigate the verification process more effectively and minimize potential hiccups that could impede their credibility.
Common Challenges in GBMS Verification
While the benefits of verification are clear, organizations often face several challenges that can complicate the GBMS verification process. Recognizing these hurdles is essential in proactively addressing them:
- Receiving the Postcard Delays: There can be significant delays in receiving verification postcards, hindering timely completion.
- Incorrect Business Information: Discrepancies in business details can lead to failed verifications, as the information must consistently match what is recorded by the platform.
- Limited Verification Options: Not all businesses may have access to multiple verification methods, posing a challenge for those seeking faster confirmation.
- Verification Code Expiry: Codes often have limited validity, meaning a fresh request may be necessary if time lapses significantly.
- Technical Issues: Users may encounter technical glitches in the platform that could hinder their verification efforts.
- Address Issues: Businesses operating from shared spaces or home offices may have a more challenging verification journey, especially in distinguishing which entity the address applies to.
By understanding these common pitfalls, businesses can devise strategies to overcome them, ensuring that their verification processes run more smoothly and efficiently.
Key Features of GBMS Verification
As organizations navigate the realm of GBMS verification, understanding key features becomes essential for establishing credibility. The following features play a vital role in enhancing the verification process:
- Comprehensive Cybersecurity: Implementing robust cybersecurity measures is crucial in safeguarding sensitive data and ensuring compliance with industry regulations.
- Multi-Factor Authentication (MFA): Utilizing MFA adds an extra layer of security, mitigating risks associated with unauthorized access.
- User-Friendly Interface: A straightforward and intuitive interface streamlines the verification process, making it accessible for businesses of any size.
- Real-Time Monitoring: The ability to monitor verification processes in real-time fosters proactive engagement with any arising issues.
- Scalable Solutions: Ensuring that verification solutions can adjust to growing organization needs is vital for sustained efficacy.
- Data Privacy Compliance: Ensuring that the verification process aligns with data protection regulations, such as GDPR, promotes user confidence.
Security Measures in GBMS Verification
As GBMS verification becomes more critical to organizational integrity, implementing robust security measures is essential to safeguard sensitive data. Here are key security considerations:
- End-to-End Encryption: Encrypting data during transmission ensures that sensitive information remains protected against unauthorized access.
- Regular Security Audits: Conducting consistent security assessments allows organizations to identify and rectify vulnerabilities promptly.
- Zero Trust Approach: Adopting a zero-trust framework mitigates risks by requiring authentication at every access point.
- Incident Response Protocols: Establishing clear incident response procedures ensures swift action in case of potential breaches, preserving company reputation.
- User Education and Awareness: Training employees in cybersecurity best practices fosters a culture of security awareness throughout the organization.
The integration of these security measures reinforces both user trust and the organization’s commitment to protecting sensitive data while navigating the complexities of GBMS verification.
Benefits of Using GBMS Verification Tools
The integration of GBMS verification tools provides organizations with several key advantages that can enhance operational efficiency and enhance user trust. Here’s a look at these benefits:
- Increased Accuracy: Verification tools improve the precision of data by uniformly checking and confirming information against reliable sources.
- Time Efficiency: Automation of verification tasks streamlines processes, minimizing manual effort and saving time.
- Error Reduction: By employing advanced algorithms, these tools reduce the likelihood of human errors in verification processes.
- Scalability: Verification tools are often designed to accommodate growing businesses, meaning they can scale efficiently in alignment with organizational needs.
- Enhanced Reporting and Analytics: Advanced reporting functionalities allow organizations to analyze their verification processes, providing insights for continual improvement.
These benefits collectively enhance organizational performance while focusing on establishing trust and ensuring reliability in business dealings.
Review of GBMS Verification Services
In exploring reviews of GBMS verification services, it’s essential to consider user experiences and feedback to ascertain areas of strength and areas needing improvement. User reviews indicate a spectrum of satisfaction, emphasizing certain key services while identifying potential shortcomings in GBMS offerings.
- Onfido: Onfido specializes in comprehensive identity verification with a user-specific focus. Customers laud its speed and reliability, rating it highly for its visibility and intuitive interface.
- Berbix: Known for its seamless photo ID verification, Berbix is favored for easing the KYC process, receiving positive feedback regarding its fraud deterrence capabilities.
- Sumsub: Sumsub earns praise for its adaptability and excellent customer support. Businesses appreciate the platform’s extensive customization options, enabling tailored verification processes.
- Persona: Persona’s scalable identity verification system is highlighted for its responsive technical support, appealing to businesses seeking a flexible yet thorough verification solution.
When compared to the mixed feedback surrounding GBMS verification services, these alternatives have showcased higher customer satisfaction rates. Users consistently seek enhancements such as reliability and service quality, which play an essential role in determining provider preference within an increasingly competitive landscape.
Comparison of Popular Verification Services
A comparative analysis of popular verification services highlights significant differences in features and user experiences. The following table summarizes key components:
| Service | Key Features | Customer Satisfaction |
| **Onfido** | Multi-ID types, rapid results, user-friendly | High |
| **Berbix** | Photo ID verification, KYC service | Moderate |
| **Sumsub** | Customizable processes, responsive support | High |
| **Persona** | Scalable solutions, easy integration, technical help | High |
The table illustrates the notable variations among different verification services, enabling businesses to make informed decisions based on specific needs. As organizations seek to bolster their verification processes, understanding the nuances of these services can aid in making strategic choices that enhance user trust and operational efficiency.
User Feedback and Experiences
User feedback provides invaluable insights into the effectiveness of GBMS verification services. Analyzing qualitative reviews showcases the spectrum of satisfaction and common pain points experienced by users.
- Positive Experiences: Many users shared successful interactions with verification services, particularly highlighting the swift processing times, intuitive interfaces, and effective customer support. Accounts often mention the helpfulness of representatives and the transparent communication facilitated by verified platforms.
- Concerns and Pitfalls: Nonetheless, some users raised concerns regarding delayed verifications, difficulties in accessing support, and discrepancies in verification results. Complaints commonly emphasize the need for improved response times and clearer communication regarding the verification process.
- Common Positive Aspects: Users commend platforms that streamline the verification process, provide real-time updates, and deliver actionable insights. The importance of a user-friendly experience is recurrent in positive reviews.
- Areas for Improvement: Constructive feedback often centers around simplifying the verification process and ensuring that all information is consistently accurate across platforms. Educational resources regarding best practices for verification are also frequently requested by users seeking improved engagement.
- Overall Sentiments: While there are mixed feelings about GBMS verification services, the feedback trends emphasize the need for continuous improvement and heightened user engagement throughout the verification processes.
As organizations strive to enhance their verification systems, paying attention to user feedback on experiences can lend clarity on actionable steps to elevate satisfaction levels and trust.
Future Trends in GBMS Verification
Looking ahead to the future of GBMS verification, several key trends are anticipated to shape how organizations approach verification processes and technologies:
- Biometric Verification Expansion: The rise of biometric technologies, such as facial recognition and fingerprint scanning, is expected to gain traction, enriching security protocols while fostering a seamless user experience.
- AI-Powered Enhancements: The integration of AI and machine learning will refine verification processes, particularly in fraud detection, thereby improving overall accuracy and automation in data verification.
- Self-Sovereign Identity (SSI): With growing consumer interest in data privacy, SSI will continue to emerge as a viable option, empowering users to control their identity data without relying on centralized entities.
- Growing Emphasis on User Experience: Organizations will prioritize user experience, aiming to balance security measures with convenience to foster trust and satisfaction.
- Regulatory Landscape Evolution: Compliance with evolving regulations will necessitate a proactive approach to GBMS verification, ensuring that organizations remain aligned with stringent guidelines.
In summary, as GBMS verification evolves, organizations must adapt to these trends, fostering innovation while maintaining a sharp focus on security and user experience to stay competitive in the marketplace.
Innovations in Verification Technology
Innovations in verification technology pave the way for more efficient and secure processes within GBMS verification. The key innovations transforming the landscape include:
- AI and Deep Learning Applications: AI-powered tools leverage deep learning methods to enhance data processing and analysis, ensuring more accurate and reliable verification outcomes.
- Blockchain Technology: Utilizing blockchain technology can enhance data security and integrity, enabling verifications that are tamper-proof and easily auditable.
- Natural Language Processing (NLP): NLP technologies improve user engagement by streamlining communication and simplifying verification-related inquiries, providing an improved user experience.
- Mobile Verification Solutions: Increasingly mobile-centric verification tools allow users to manage their verification processes through smartphones, ensuring accessibility and convenience.
- Predictive Analytics: The use of predictive analytics in verification processes allows organizations to anticipate risks or verify credentials efficiently, improving response times.
These innovations underscore the dynamic nature of verification technology, highlighting the ongoing commitment to enhancing security, efficiency, and user satisfaction as organizations strive to remain at the forefront of the GBMS verification landscape.
Predictions for GBMS Verification in 2025
As we look ahead to 2025, several predictions are set to shape the future of GBMS verification:
- Comprehensive Security Frameworks: Expect a greater emphasis on creating robust cybersecurity frameworks that incorporate multi-layered security measures to address evolving threats.
- Seamless User Experiences: Organizations will prioritize user experience, ensuring verification processes are not only secure but also convenient. The integration of streamlined interfaces will foster user engagement while minimizing friction.
- Heightened Regulatory Compliance: Businesses will adapt to increasingly stringent regulations surrounding data protection, necessitating enhanced verification practices that align with global standards.
- Data Decentralization: The shift toward decentralized verification systems may gain traction, empowering users with ownership and control over their data without relying on centralized authorities.
- AI-Driven Insights: By 2025, AI will play an even more significant role in verification analytics, enabling organizations to glean actionable insights from verification data, enhancing strategy development.
Overall, the 2025 landscape is likely to be characterized by innovation, enhanced security measures, and a commitment to user-focused experiences, ensuring that GBMS verification continues to evolve and adapt to the changing needs of the industry.
Conclusion
As we’ve explored throughout this article, the verification processes associated with Global Business Management Systems carry immense importance across various dimensions, particularly in building and maintaining user trust, safeguarding data integrity, and enhancing business reputation. The reliability of GBMS verification stands as a crucial point of contention in fostering long-term relationships between businesses and their users.
By adhering to a comprehensive verification process that incorporates advanced technologies, businesses can champion integrity and transparency while adapting to evolving trends. This adaptive agility will enable enterprises to navigate challenges more effectively, bolstering user satisfaction and loyalty. The landscape of GBMS verification continues to see significant innovations aimed at enhancing effective security measures, user engagement, and compliance with regulatory standards.
As we venture forward, organizations that consistently prioritize clarity, user experiences, and technologically advanced safeguards within their verification processes will likely emerge as industry leaders. By exploring the trends, innovations, and choices shaping GBMS verification, companies can proactively position themselves for success and cultivate deeper connections with their audiences in this increasingly digital world.
Frequently Asked Questions:
Business Model Innovation:
Embrace the concept of a legitimate business! Our strategy revolves around organizing group buys where participants collectively share the costs. The pooled funds are used to purchase popular courses, which we then offer to individuals with limited financial resources. While the authors of these courses might have concerns, our clients appreciate the affordability and accessibility we provide.
The Legal Landscape:
The legality of our activities is a gray area. Although we don’t have explicit permission from the course authors to resell the material, there’s a technical nuance involved. The course authors did not outline specific restrictions on resale when the courses were purchased. This legal nuance presents both an opportunity for us and a benefit for those seeking affordable access.
Quality Assurance: Addressing the Core Issue
When it comes to quality, purchasing a course directly from the sale page ensures that all materials and resources are identical to those obtained through traditional channels.
However, we set ourselves apart by offering more than just personal research and resale. It’s important to understand that we are not the official providers of these courses, which means that certain premium services are not included in our offering:
- There are no scheduled coaching calls or sessions with the author.
- Access to the author’s private Facebook group or web portal is not available.
- Membership in the author’s private forum is not included.
- There is no direct email support from the author or their team.
We operate independently with the aim of making courses more affordable by excluding the additional services offered through official channels. We greatly appreciate your understanding of our unique approach.
Be the first to review “GMBs Verification 2024” Cancel reply
You must be logged in to post a review.
Related products
Business
Business










Reviews
There are no reviews yet.